2023 Gartner® Magic Quadrant™ for Endpoint Protection Platforms
Mehr erfahrenIn einer hypervernetzten Welt, in der Cyberangreifer niemals schlafen und Unternehmen mit unvorhersehbaren Risiken konfrontiert sind, sorgt Bitdefender für Widerstandsfähigkeit.
Wir bieten:
Zentralisierte Endpunktsicherheit und -analyse - über Endpunkte und hybride Workloads hinweg mit unkomplizierter Verwaltung
Unübertroffene Angriffsprävention - Technologien und maschinell lernende Algorithmen erkennen und verhindern noch mehr Angriffe
Experten, die Verantwortung übernehmen - Rund-um-die-Uhr-Sicherheitsbetrieb mit vordefinierten Reaktionsplänen
Eingebaute Threat Intelligence der Extraklasse - Bedrohungsforschung an vorderster Front, zusammen mit Strafverfolgungsbehörden und Forschungseinrichtungen
Eine lohnende Investition - wir nehmen Cybersicherheit den Schrecken der Komplexität und senken bei höchster Sicherheit noch Ihre Kosten
Entscheiden Sie sich für unsere Sicherheitsplattform oder unseren Managed Service, um Ihr Unternehmen widerstandsfähiger gegen Cyberangriffe zu machen.
Versetzen Sie Ihr Unternehmen in die Lage, Bedrohungen besser abzuwehren und so den Geschäftsbetrieb jederzeit aufrechtzuerhalten.
Mehr erfahrenTechnologien und Datensicherheitsvorschriften entwickeln sich immer weiter. Ohne die richtigen Technologien für die Sicherheits-Compliance ist eine Umsetzung jedoch kaum möglich.
Mehr erfahrenLassen Sie sich die Umsatzpotenziale durch die gesteigerte Nachfrage nach Managed Security nicht entgehen. Überzeugen Sie am Markt mit fortschrittlichsten Security-Technologien und setzen Sie auf ein einfaches und kosteneffektives Geschäftsmodell, um Ihre Gewinne zu maximieren.
Mehr erfahrenSicherheit ist die Herausforderung Nr. 1 in der Cloud. Immer mehr Unternehmen steigen immer schneller auf neue Geschäftsmodell um und führen in diesem Zuge neue, cloudbasierte Unternehmensplattformen ein. In Verbindung mit zunehmend dynamischen Workloads führt das dazu, dass klassische Sicherheitstools einfach nicht mehr Schritt halten können.
Mehr erfahrenBereits 80 % der Unternehmen verfolgen eine hybride Cloud-Strategie. Die Marktforscher von Gartner® wissen: "Eine agile und effiziente Infrastruktur beginnt im Rechenzentrum. Egal, ob modernes softwaredefinierte Rechenzentrum oder integrierter Ansatz mit hybrider Cloud, Unternehmen müssen ihre Rechenzentren wirksam vor Risiken schützen, um Resilienz und Wettbewerbsfähigkeit zu gewährleisten."
Mehr erfahrenKompromittierten Endpoints sind Ausgangspunkt für mehr als die Hälfte aller Sicherheitsverletzungen. Die Angriffsfläche auf Ihren Endpoints wächst stetig. Modernisieren Sie Ihre Endpoint-Sicherheit, um auch in Zukunft komplexen Angriffen standhalten zu können.
Mehr erfahrenSchützen Sie Ihr Unternehmen vor Cyberbedrohungen und setzen Sie auf eine führende Sicherheitslösung, die unkompliziert zu verwalten ist und mit attraktiver Preisgestaltung überzeugt.
Mehr erfahrenEntlasten Sie Ihre IT- und Sicherheitsteams mit einem Service, der branchenführend Sicherheitstechnologien mit einem fortschrittlichen Sicherheitsbetrieb vereint, der rund um die Uhr für Sie Einsatz ist.
Mehr erfahren
Komplexe Cyberangriffe sind heute an der Tagesordnung und der Erfolg Ihres Unternehmen hängt auch von Ihrer Fähigkeit ab, sich auch von Angriffen nicht aufhalten zu lassen. Bitdefender GravityZone vereint Risikoanalysen mit Härtung, Bedrohungsabwehr, Erkennung und Reaktionsmöglichkeiten, um die Cyberresilienz Ihres Unternehmens zu stärken.

Bitdefender hilft Ihnen dabei, HIPPA-Vorschriften und DSGVO-Sicherheitsstandards zuverlässig und ohne großen Aufwand einzuhalten. Mit Bitdefender erhalten Sie zum Umgang mit Sicherheitsvorfällen die Steuerungsmöglichkeiten, Nachvollziehbarkeit und revisionssicheren Daten, die Sie benötigen, um Sicherheits-Compliance einfach und wirksam zu gewährleisten.

Bitdefender GravityZone überzeugt durch Einfachheit und Flexibilität und ist ideal geeignet, um marktführende Managed Security Services anzubieten. Die integrierte Lösung kombiniert in einzigartiger Weise Härtung, Prävention und Erkennung der Spitzenklasse und benötigt dafür nur eine zentrale Konsole. So können Sie eine Vielzahl von Assets und Umgebungen effizient schützen und jederzeit schnell reagieren, ohne Ihre Ressourcen zu belasten.

Bitdefenders Lösung wurde eigens für die besonderen Anforderungen an die Sicherheit von Server-Workloads und von Cloud-nativen Anwendungen entwickelt. Sie bietet leistungsstarke Cloud Workload Security (CWS) und Automatisierung dank zahlreicher Integrationen. So kann die Sicherheit zunehmend heterogener IT-Landschaften konsolidiert verwaltet werden, egal ob Hybrid oder Multi-Cloud, Linux, Windows oder Container.

Mit Bitdefenders Sicherheitslösungen für Rechenzentren gewährleisten Sie cloudübergreifend durchgehende und zuverlässige Sicherheit für Ihre Server und virtuellen Desktops. Dank Automatisierung gewinnen Sie ein Plus an Agilität und können so den Zeitaufwand für die Verwaltung Ihrer Sicherheit von Tagen auf wenige Stunden reduzieren. Anders als herkömmliche Endpoint-Sicherheitslösungen werden beim Bitdefender-Ansatz zentralisierte Scan-Aufgaben an dedizierte virtuelle Appliances ausgelagert, wodurch in erheblichem Maße Ressourcen freigesetzt werden. Tests haben eine Steigerung der Virtualisierungsdichte um bis zu 55 % und eine Beschleunigung der Anwendungsleistung um bis zu 36 % belegt.

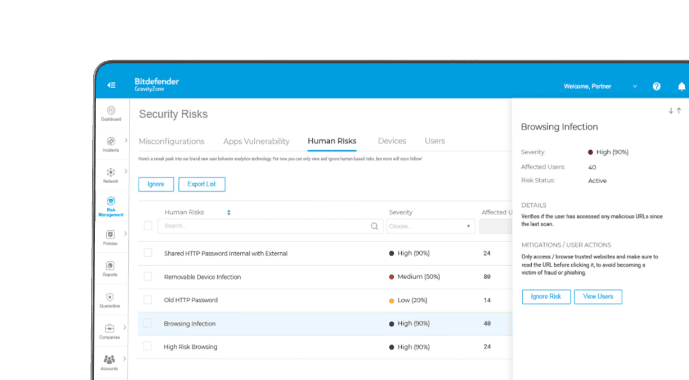
Bitdefenders umfassender Technologie-Stack zum Schutz Ihrer Endpoints hilft Ihnen, Ihre Strategie und Architektur für die Endpoint-Sicherheit zu erweitern. Sie erhalten mehrstufigen Endpoint-Schutz, der die Angriffskette unterbricht, unterstützt durch Funktionen zur schnellen Abhilfe sowie Möglichkeiten, das Risiko durch den Faktor Mensch zu erfassen und entsprechende Maßnahmen abzuleiten.

Die hochmoderne Sicherheitslösung für kleine Unternehmen minimiert die Gefahr von Sicherheitsverletzungen, die Ihre Systeme beeinträchtigen und sogar Ihren Geschäftsbetrieb unterbrechen könnten. Mit GravityZone sind Ihre Endpoints rundum geschützt und Sie haben die Gewissheit, dass Sie sich für eine Lösung entschieden haben, die herkömmliche Mittelstandslösungen weit hinter sich lässt.

Mit Managed Detection and Response (MDR) von Bitdefender lagern Sie ihren Sicherheitsbetrieb an uns aus und erhalten Sie ganzjährig, rund um die Uhr zuverlässige Sicherheit. Unser MDR-Dienst vereint Cybersicherheit für Endpoints sowie Netzwerk- und Sicherheitsanalysen mit der Expertise von erfahrenen Bedrohungsjägern in einem SOC, das mit Sicherheitsanalysten aus aller Welt besetzt ist.
Gewährleistet für alle Endpoints, Produktivitätsanwendungen, Identitäten, Netzwerke und hybriden Cloud-Workloads höchste Wirksamkeit, ein breites Spektrum an Sicherheitsfunktionen und intuitive Verwaltung.
Die Präventionstechnologien und maschinellen Lernmodelle von Bitdefender erkennen und unterbinden Angriffe rechtzeitig. Wir werden nicht erst aktiv, wenn es längst zu spät ist.
Kombiniert moderne Bedrohungsabwehr mit vorgedachten Analysen und umfangreichen Sicherheitskontext zur Korrelation isolierter Warnmeldungen, schnellen Priorisierung von Vorfällen und Eindämmung von Angriffen durch automatisierte und geführte Reaktionsmaßnahmen.
Angreifer schlafen nicht und deshalb ist auch unser Security Operations Center (SOC) rund um die Uhr für Sie im Einsatz. Und wenn wir Sie um 3 Uhr morgens anrufen müssen, dann präsentieren wir Ihnen mit dem Ticket auch gleich eine Lösung.
Erfahren Sie, wie Sie die Cyber-Resilienz Ihres Unternehmens durch zentralisierte Endgerätesicherheit und -analysen, Angriffsprävention, Rund-um-die-Uhr-Sicherheitsoperationen und aktuelle Bedrohungsdaten erhöhen können.
Lernen Sie, was es bedeutet, in einer hypervernetzten Welt, in der Cyberkriminelle niemals schlafen und Unternehmen mit unvorhersehbaren Risiken konfrontiert sind, wirklich resilient zu sein.
In unserem Erklärvideo sehen Sie, wie Sie Cyber-Sicherheitsrisiken vorbeugen und die eigene Resilienz stärken können, ohne neue Mitarbeiter einstellen oder teure Tools und Services von verschiedensten Anbietern kombinieren zu müssen.
Vereinfachen Sie Ihre Sicherheitsarchitektur mit einem Sicherheitspaket, das sich an Ihren Anforderungen orientiert. Sind Sie auf der Suche nach einer einfachen und kostengünstigen Sicherheitslösung? Oder möchten Sie Ihren Schutz automatisieren, ohne auf Leistungsfähigkeit zu verzichten? Oder soll es eine allumfassende Lösung für die Endpoint-Sicherheit sein, die darüber hinaus Posture Management, fortschrittliche Prävention sowie EDR umfasst?

Bitdefender MDR schützt Unternehmen, indem es ihre Sicherheit rund um die Uhr überwacht, auch komplexeste Angriffe verhindert, erkennt und behebt und mit einem SOC-Team aus erfahrenen Sicherheitsexperten Bedrohungen aktiv aufspürt.

Sicherheitslösungen für physische, virtuelle und Cloud-Umgebungen lassen Sie entscheiden, welche Sicherheitstechnologien Sie zur Optimierung Ihre Sicherheitsarchitektur einsetzen möchten.

Die MSP-Sicherheitsprodukte von Bitdefender ermöglichen es Ihrem Unternehmen, sich von der Konkurrenz abzuheben und Ihre Gewinne zu steigern - mit bestbewerteten Schutz, monatlichen MSP-Lizenzen und einer zentralen, intuitiven Verwaltungskonsole.
1600+
Mitarbeiter in aller Welt
Gegründet 2001, Kunden in 170 Ländern, 440 Patente (Tendenz steigend)
400+
pro Minute gefundene Bedrohungen
180
im Einsatz bei den den bekanntesten Technologiemarken der Welt
